Single Sign On With Pingidentity
25 May 2024 - sj, tags: archiving, insights, news, product
In this article we’ll discuss how to use SSO authentication against PingIdentity.
Setup PingIdentity SSO
We assume you have a PingIdentity account.
Create a new environment
Click on the blue add icon, then select “Build your own solution”, and select “PingOne SSO”. Click on “Next”.
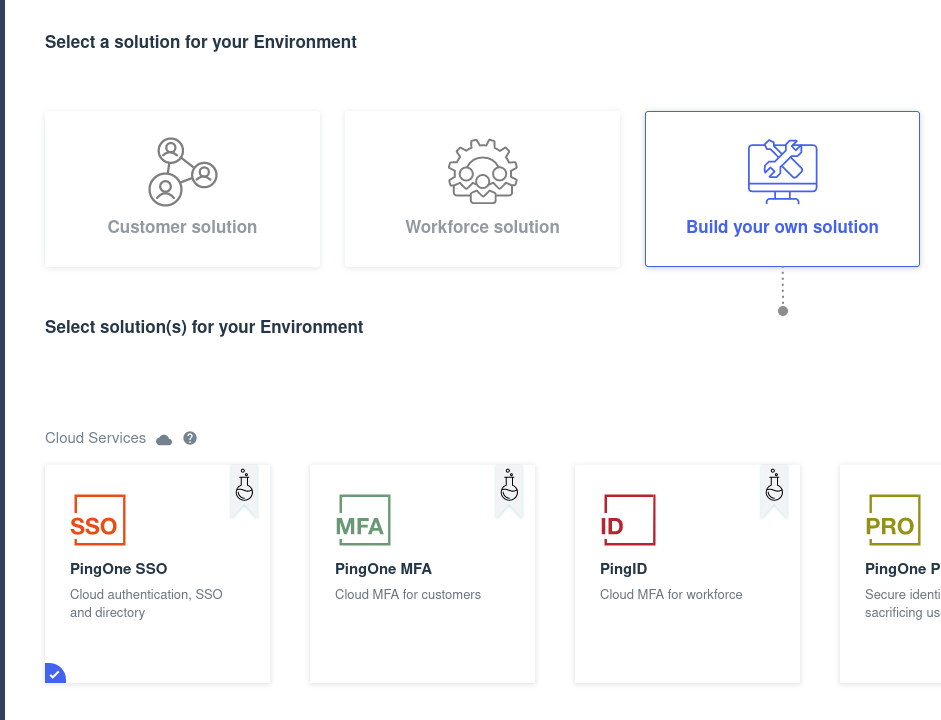
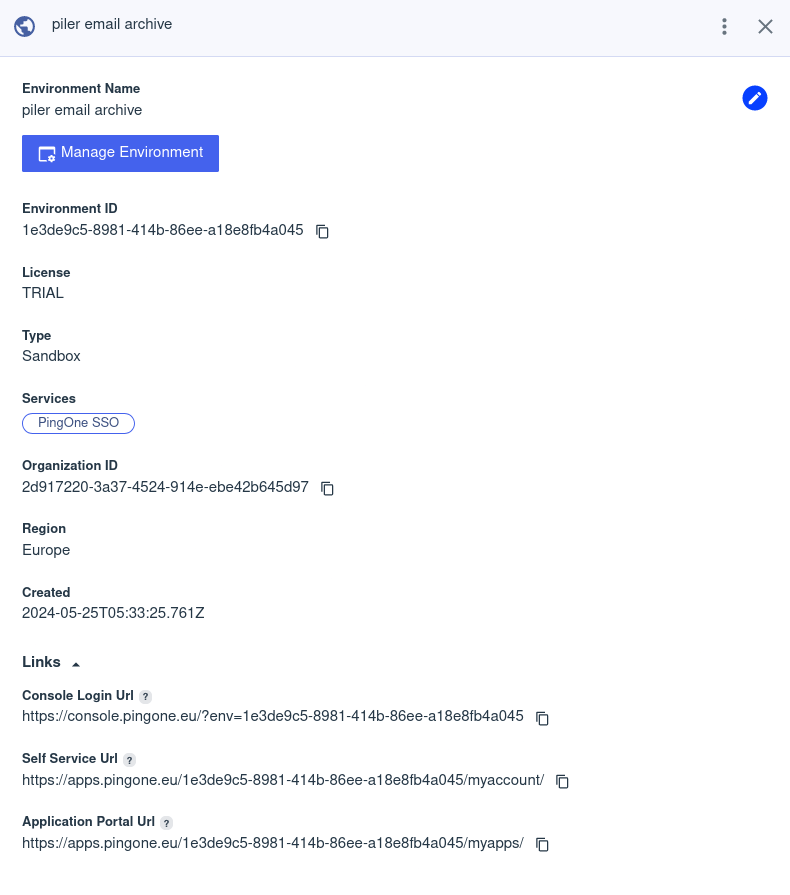
Give the environment a name, select the region, etc. then click “Finish”.
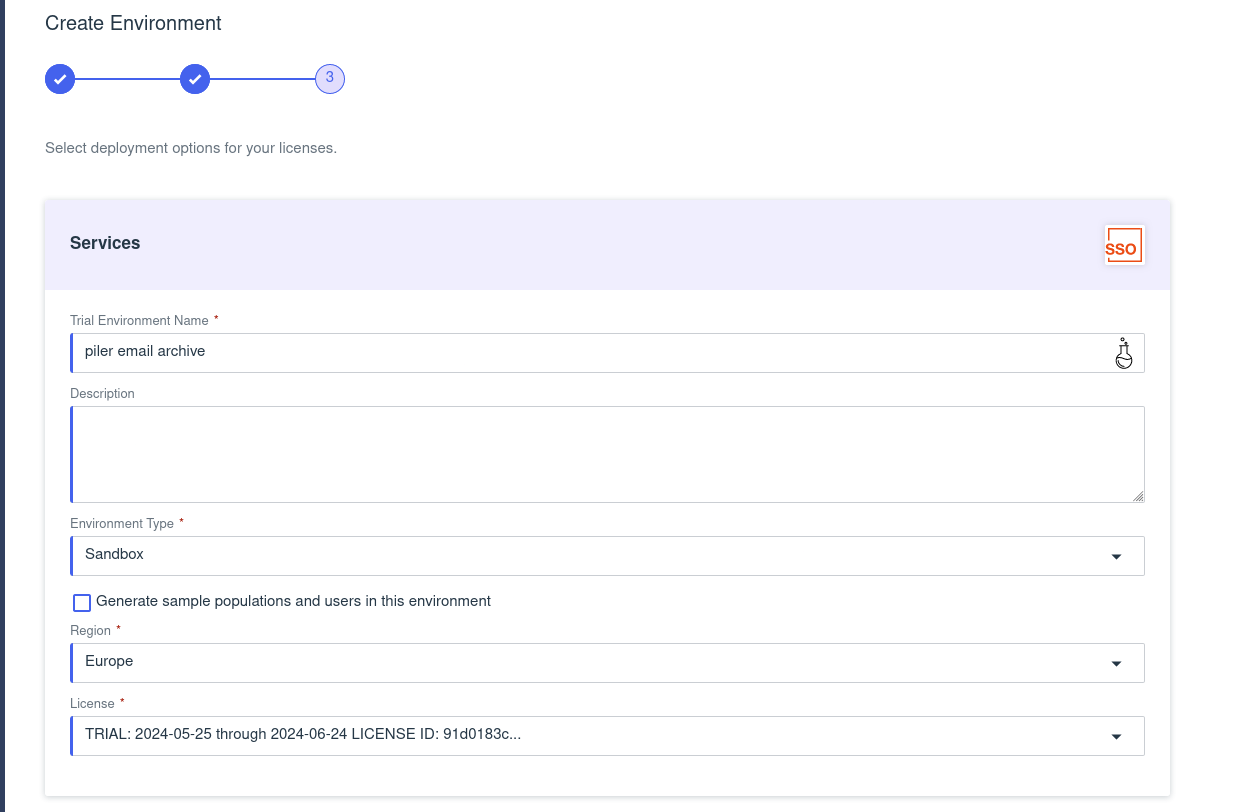
Click on the created environment, then click on “Manage environment” button.
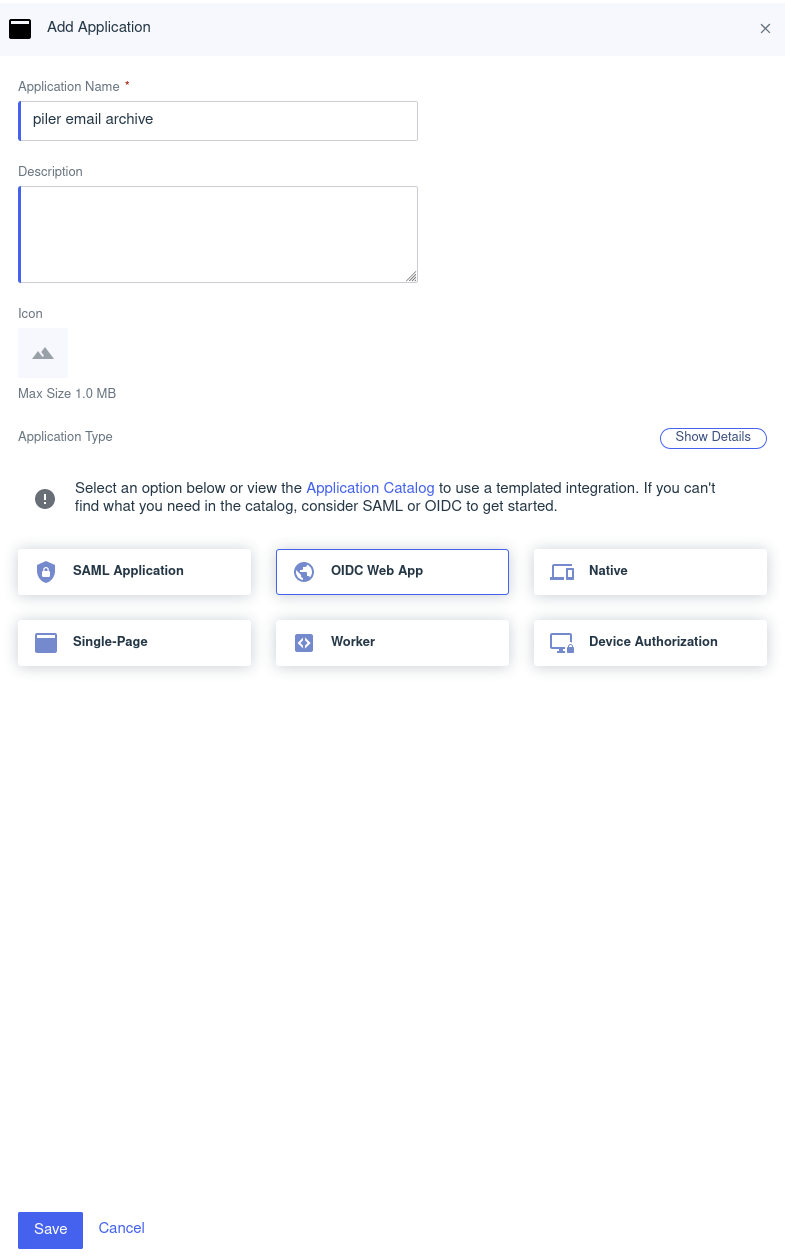
Create new application
Give a name to the application, eg. “piler email archive”, and select “OIDC web app”, then click on Save.
Get the client id and client secret values.
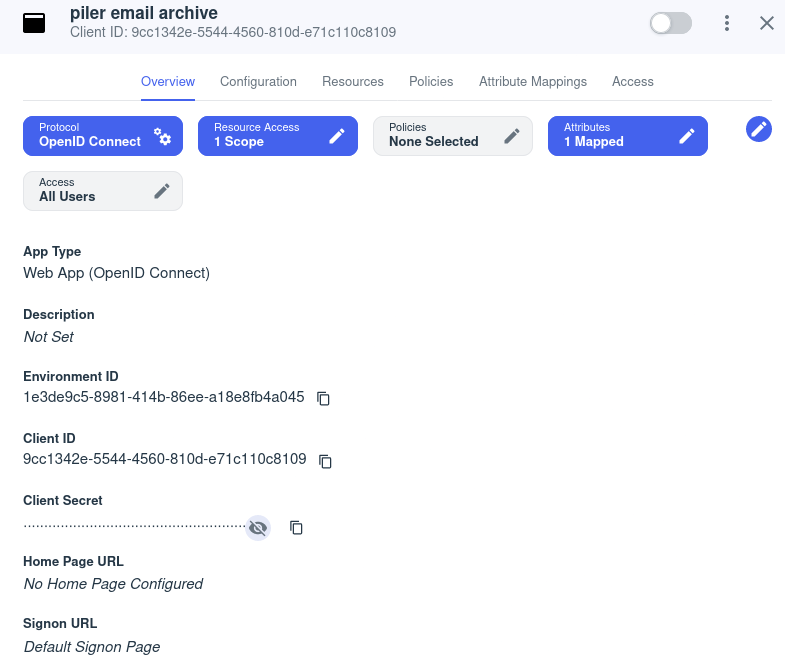
Add them to /etc/piler/config-site.php:
$config['ENABLE_PINGIDENTITY'] = 1;
$config['PINGIDENTITY_CLIENT_ID'] = '9cc1342e-5544-4560-810d-e71c110c8109';
$config['PINGIDENTITY_CLIENT_SECRET'] = '_r8pmC-nHgX5AEVDQ~0xMz_HWd5NXHgE2vQWNkgw3vc87GV.roBb1gn';
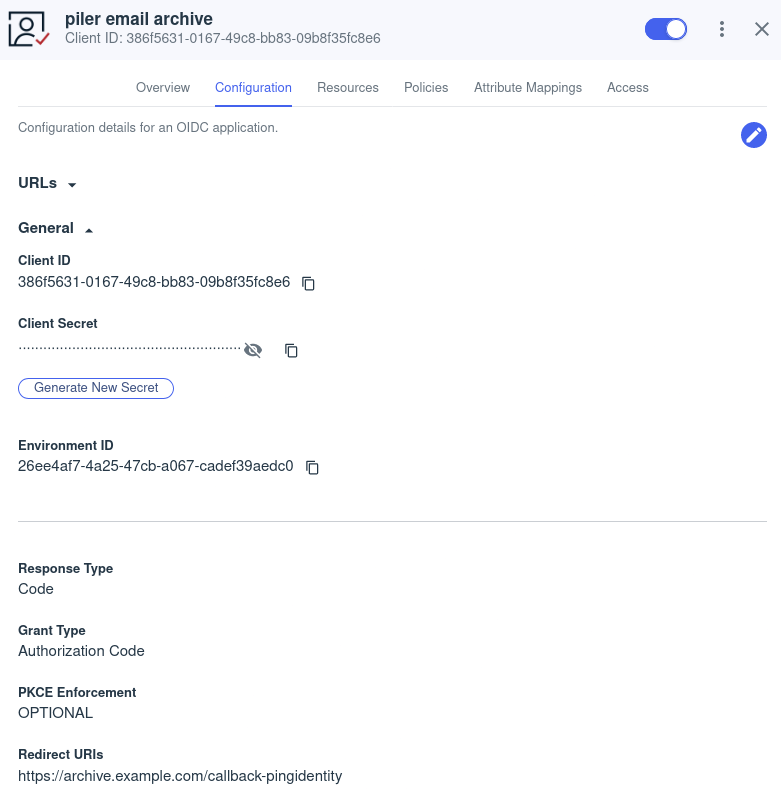
In the configuration menu, set following:
- Response type: Code
- Redirect URIs: https://archive.example.com/callback-pingidentity
- Token Auth Method: Client Secret Post
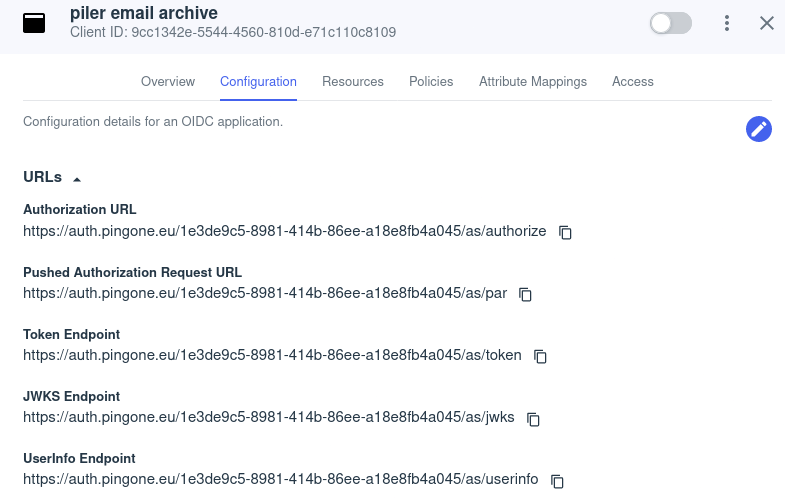
Click on the URLs dropdown and write the following URL values to /etc/piler/config-site.php:
$config['PINGIDENTITY_AUTHORIZE_URI'] = 'https://auth.pingone.eu/1e3de9c5-8981-414b-86ee-a18e8fb4a045/as/authorize';
$config['PINGIDENTITY_TOKEN_URI'] = 'https://auth.pingone.eu/1e3de9c5-8981-414b-86ee-a18e8fb4a045/as/token';
$config['PINGIDENTITY_USERINFO_URI'] = 'https://auth.pingone.eu/1e3de9c5-8981-414b-86ee-a18e8fb4a045/as/userinfo';
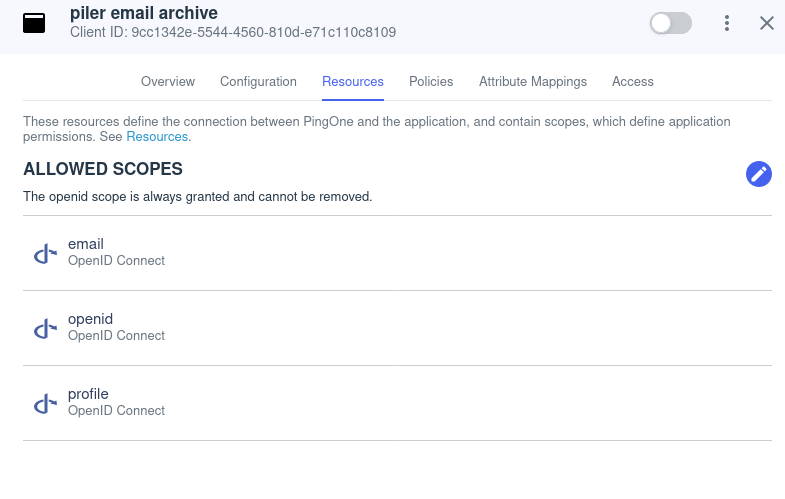
Set the following scopes for the application
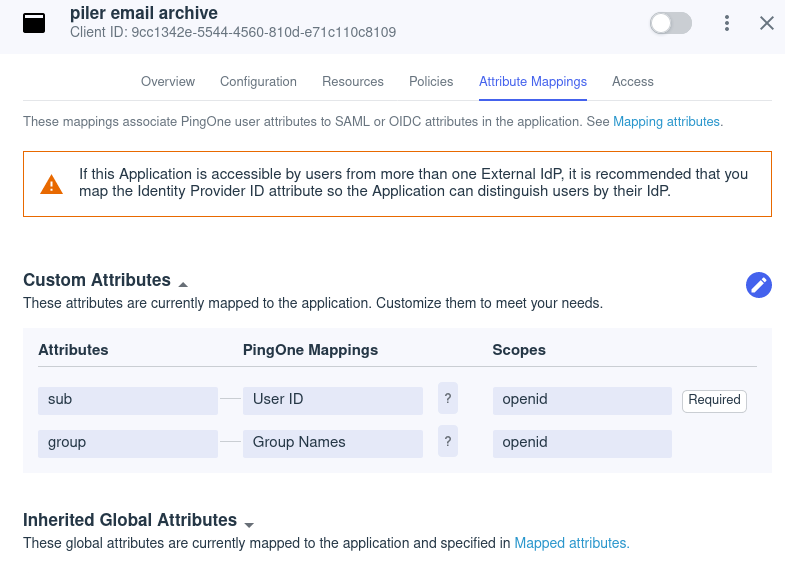
Update the attributes mapping to include the group names
Create a group
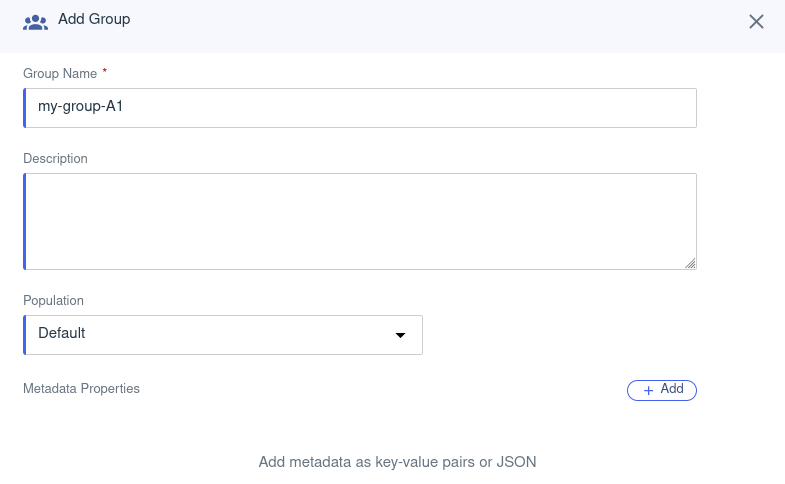
Create a user
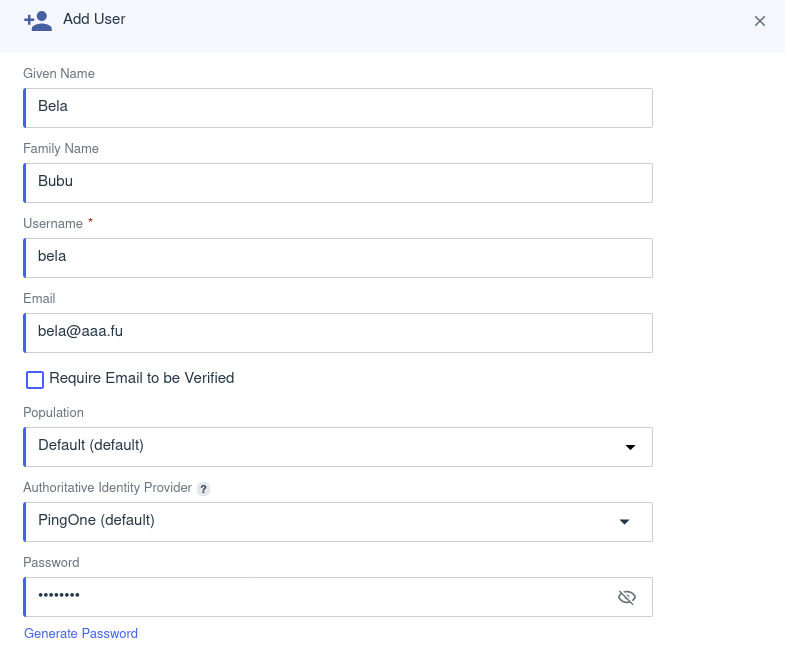
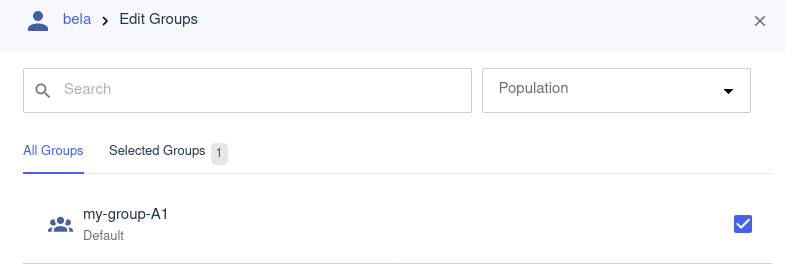
Edit the user and assign it with the group we created just above.
Login to the archive
Let the users click on the fingerprint icon with the text “ping identity”.
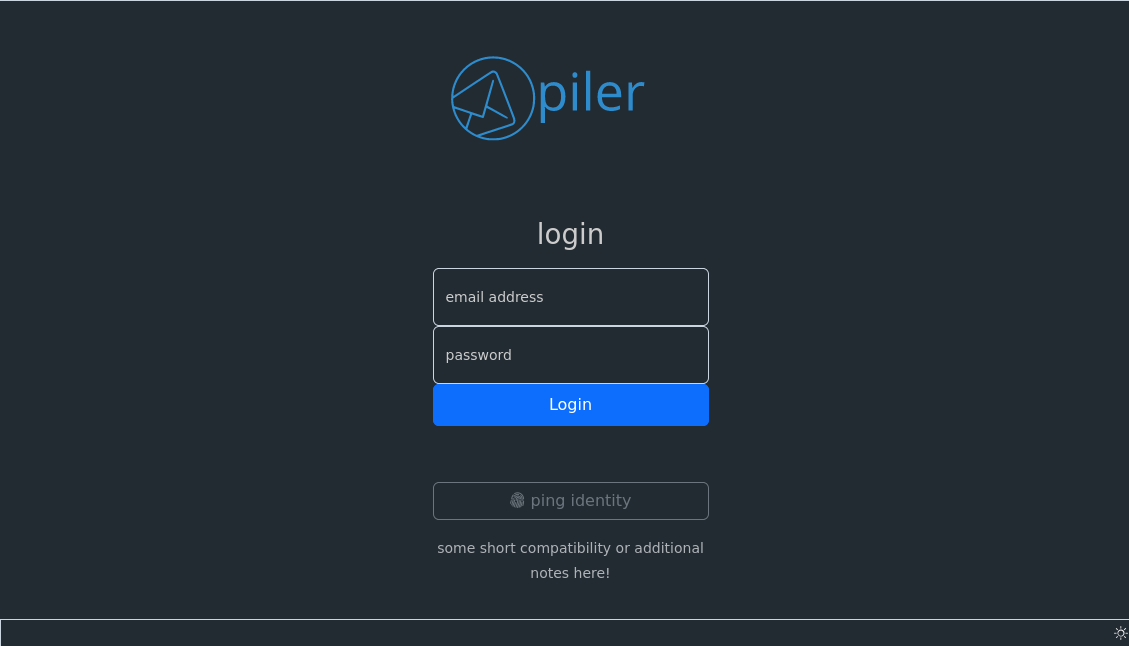
The link takes them to PingIdentity where they authenticate themselves.
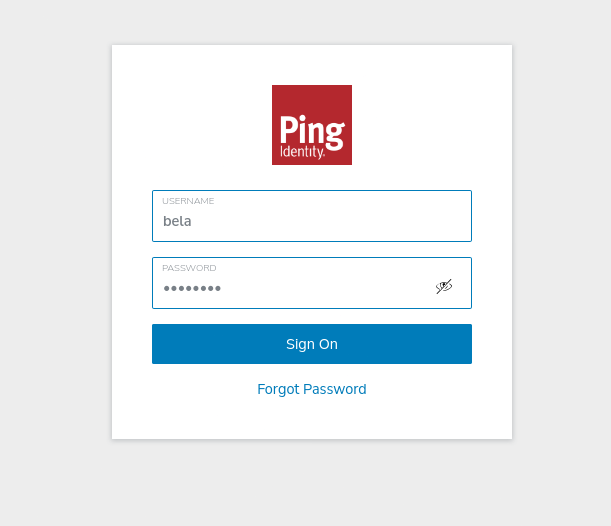
After a successful authentication they are redirected back to the piler GUI.
In case the user wants to change his own password or setup 2FA, then he may visit the Self Service Url.
Conclusion
You have secured the authentication using SSO to the piler GUI with PingIdentity.

