Using Azure Ad Single Sign On Sso
06 Apr 2021 - sj, tags: archiving, insights, news, product
Azure is a popular cloud provider, and the piler GUI supports Azure AD to provide Single Sign-On (SSO). In this article we’ll see how to delegate the piler GUI authentication to Azure AD using its SSO capabilities.
Prerequisites
You have an Azure subscription or trial, you have created users and preferably groups in the appropriate Azure tenant.
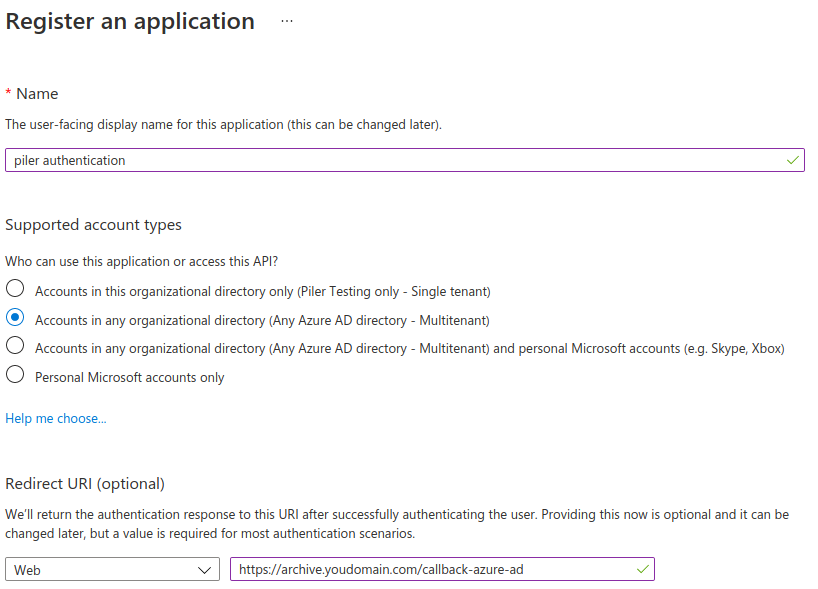
Click on “App registration“, enter a name for the application, select “Any Azure AD directory – Multitenant” at the supported account types, and set the “Redirect URI“. Be sure to replace “archive.yourdomain.com” with your archive FQDN. Finally record the application (client) id value.
Setup the application in Azure
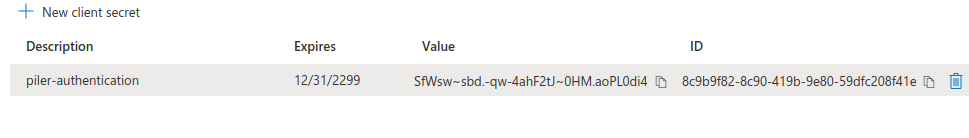
Click “Certificates and secrets”, create a new client secret, and record the secret value.
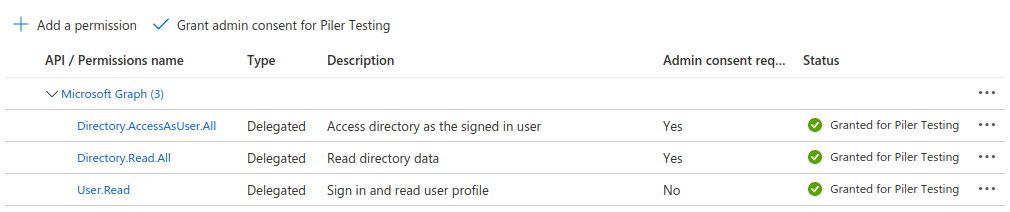
Select “API permissions”, and add the following permissions, then click on the “Grant Admin consent for …” button
Configure the piler GUI to allow Azure AD authentication
Edit /etc/piler/config-site.php or the site specific config if you have the multitenant license, and set the following:
$config['ENABLE_AZURE_AD'] = 1;
$config['AZURE_AD_CLIENT_ID'] = '1b0a2f95-6630-4992-a561-4c38e33eed23';
$config['AZURE_AD_CLIENT_SECRET'] = 'SfWsw~sbd.-qw-4ahF2tJ~0HM.aoPL0di4';
Let the users log in
Users will see the “Azure AD” link on the login screen.
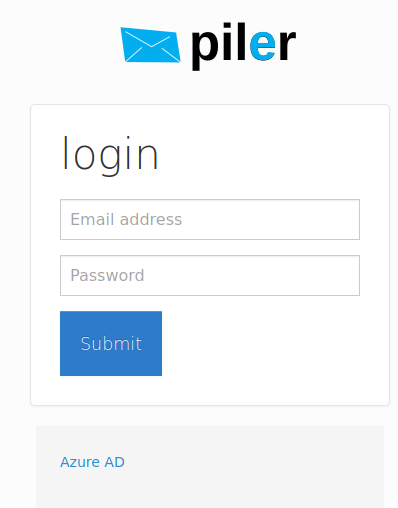
After clicking on it the user is redirected to Azure for authentication. After providing his credentials, he’s redirected back to the piler gui.
He also has his group assignments from Azure. “group1” and “mygroup1111” are inherited from Azure AD, “group2” is a local, piler group.